ICTOM CYBERSECURITY
We seamlessly integrate logical and physical safeguards to ensure your organization's safety by protecting individuals and data
Security Assessment and Testing
We offer you the best technical testing, and examination, methods and techniques that your organization might use as part of an security assessment.
We guarantee you a positive impact on the security posture of your systems and ultimately your entire organization.

Our approach will help you to
1 - Establish an information security assessment policy, that identifies your organization's specific requirments and implements accountability for its idividuals to ensure compliance, roles and responsibilities
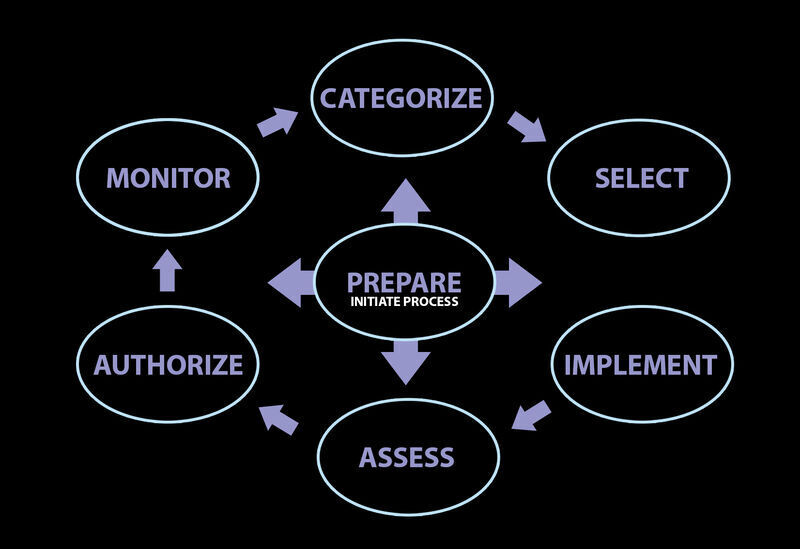
2 - Implement a documented assessment methodology to establish consistency and structure to assessments. This allow you to expedite the transition of new assessment staff, and addresses resource constraints while minimizing risks introduced by assessment techniques.
3 - Formulate the objectives of each security assessment, and adapt the approach accordingly. We will use a combination of techniques to draw a global picture of your ogranization's security and limit risk and resource usage
4 - Analyze findings, and develop risk mitigation techniques to address weaknesses. We will conduct root cause analysis upon completion of assements and translate technical findings into actionable mitigation techniques for technical flaws and weaknesses in processes and procedures
Let’s take your security to the next level.

To gather information about assets to be tested, the threats of interest against them, and the security controls to be implemented to mitigate the threats. Our assessment procedures allow you to clarify
=> Organizational requirements with which assessments must comply=> Appropriate roles and responsibilities
=> Adherence to established methodology
=> Assessment frequency
=> Documentation requirements(assessment plans and results)
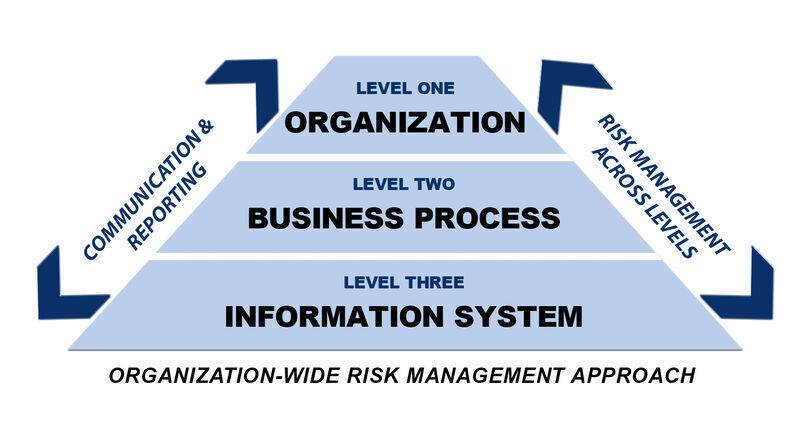
As an Information and Communication Technology Organization, we thrive by guiding our customers from different industries all around the world. Wether you need to integrate a new software, build a cybersecurity strategy or redesign/upgrade a technological solution. We can help you !